How-To: encrypted partitions over LVM with LUKS — page 3 — install and config
4. Installing the system
we are now going to install the distro over our layout. Start the installer and make sure you choose manual partitioning. Then set up your filesystem like the one on the screenshot.
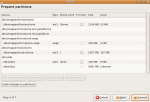
When the installer has finished, do not reboot yet
5. Configuring the installed system
As we force the system to be installed on our custom partitions, and because Ubuntu desktop livecd is not aware of lvm and encryption, we need to customize the system that has just been installed. To achieve this, we will chroot into our future system and mount the required partitions.
# mkdir /target
# mount /dev/mapper/rootvolume /target/
# mount /dev/mapper/homevolume /target/home
# mount /dev/sda1 /target/boot
# chroot /target
# mount -t proc proc /proc
# mount -t sysfs sys /sys
Now, we will install the required software to be able to handle encryption and lvm:
# apt-get install lvm2 cryptsetup
then, we need to inform cryptsetup on how to mount our encrypted partitions. The settings happens in /etc/crypttab:
# <target name> <source device> <key file> <options>
rootvolume /dev/lvmvolume/encryptedroot none luks,retry=1
homevolume /dev/lvmvolume/encryptedhome none luks,retry=1
Also, if we want our system to be able to mount the partitions, the initrd needs to contains modules for lvm, and encryption. This is handled by /etc/initramfs-tools/modules. So edit it and add:
aes-i586
dm-crypt
dm-mod
sha256
And finally, another last step: editing fstab
This next step has to be done, otherwise, your system won’t boot!!!
It looks like the kernel is not match the UUID with the actual logical device. So, for each of your encrypted partition, change the UUID=asas-asa-sasas by the actual device: /dev/mapper/mydevice. For instance, in this tutorial, my final /etc/fstab looked like this:
# /etc/fstab: static file system information.
#
# <file system> <mount point> <type> <options> <dump> <pass>
proc /proc proc defaults 0 0
# /dev/mapper/rootvolume
#UUID=af21a76e-3a85-4ca5-a6b9-e362d97892ba
/dev/mapper/rootvolume / ext3 relatime,errors=remount-ro 0 1
# /dev/sda1
UUID=2de459f5-306a-4d57-bd5c-76eb50c81179 /boot ext2 relatime 0 2
# /dev/mapper/homevolume
#UUID=443a67f1-2ee1-43bc-b248-882b5068cc24
/dev/mapper/homevolume /home ext3 relatime 0 2
# /dev/mapper/lvmvolume-swap
UUID=d4f44b82-0d73-4269-af68-a613f11876fe none swap sw 0 0
/dev/scd0 /media/cdrom0 udf,iso9660 user,noauto,exec,utf8 0 0
/dev/fd0 /media/floppy0 auto rw,user,noauto,exec,utf8 0 0
And regenerate the initrd file with:
# update-initramfs -k all -c
you can verify that the initrd contains the correct information to mount the encrypted partition:
# mkdir /tmp/tmp
# cd /tmp/tmp
# zcat /boot/initrd.img-`uname -r` | cpio -iv
# cat conf/conf.d/cryptroot
target=rootvolume,source=/dev/lvmvolume/encryptedroot,key=none
Well, that’s about it, you should now reboot your computer, and hopefully you will get a screen like the screenshot prompting you for a password. If the progress bar seems to hang for quite some time, chances that either /etc/fstab or /etc/crypttab is not properly set up. In that case, you will need to boot on the live cd again, install the packages lvm2 and cryptsetup, run lvchange -ay , reopen the partitions and mount them….. and find what is wrong… a lot of pleasure. If you are lucky enough :), type your password to unlock / first then another time for /home and voila, you are running ubuntu on an encrypted filesystem.
There is ways to plug in a removable media containing a key file to unlock the partitions. This will be covered in another tutorial.
